The Risk Management Framework (RMF) provides a 7-step repeatable process used to identify, mitigate and monitor risk within information systems and organizations. The RMF process is managed by the National Institute of Standards and Technology (NIST) under the Federal Information Security Modernization Act (FISMA) and applies to all US federal information systems. While originally adopted by US federal agencies, RMF can easily be applied to all organizations in both the public and private sector.
Why All Federal Contractors Need To Know The Risk Management Framework
FISMA requires all federal agencies, state agencies and federal contractors working with a federal information system to develop, implement and continuously monitor a risk-based approach to managing information security risk. NIST, under the direction of FISMA, is responsible for updating and maintaining compliance documents to provide the guidance agencies need to meet FISMA requirements. The Risk Management Framework is one of these documents under NIST's guidance.
What Are The FISMA Requirements?
FISMA compliance requires agencies to implement and monitor information security controls throughout the organization. More specifically, FISMA requires each federal agency to:
- Inventory all active systems and integrations
- Categorize their risk
- Develop and regularly update a security plan
- Implement the appropriate security controls according to NIST 800-53
- Perform a 3-tiered risk assessment (RMF) every time a system is changed
- Conduct annual security reviews
The Risk Management Framework Process
As mentioned previously, the RMF process can be used within any type of organization. Additionally, it can be applied to any type of new or legacy system. Below, we outline each step of the Risk Management Framework.
RMF Step 0: Prepare
This first step in the Risk Management Framework is designed to prepare the organization for what will come with the remaining RMF steps. It also focuses on developing an organization-wide risk assessment and strategy.
Learn More About Step 0 From NIST Guidance
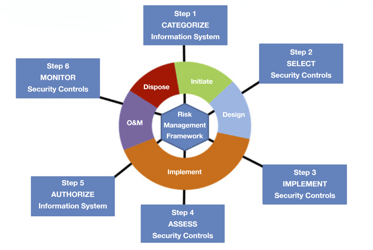
RMF Step 1: Categorize
The Categorize stage focuses on determining a systems' potential loss of confidentiality, integrity and availability and its subsequent adverse impact to the organization. Understanding these elements better informs the following risk management processes and tasks.
Learn More About Step 1 From NIST Guidance
RMF Step 2: Select
Step 2 focuses on the selection, customization and documentation of the security and privacy controls necessary to protect the system and organization in relation to its risk.
Learn More About Step 2 From NIST Guidance
RMF Step 3: Implement
During this stage, the selected security and privacy controls are implemented and working to protect the system as expected.
Learn More About Step 3 From NIST Guidance
RMF Step 4: Assess
The Assess stage marks the beginning of the ongoing operations and maintenance of the system. In regards to newly implemented controls, this phase the examines the recently implemented security and privacy controls to verify they are working as intended. After this initial assessment, controls are assessed on an ongoing basis, as outlined in the organization/system's unique continuous monitoring plan. These assessments provide the information necessary to determine whether or not a system should continue to operate. In some cases, an independent third-party assessor may be required to perform this step.
Learn More About Step 4 From NIST Guidance
RMF Step 5: Authorize
NIST defines the Authorize step as one that "provides organizational accountability by requiring a senior management official to determine if the security, privacy, and supply chain risk to organizational operations, assets, individuals, other organizations, or the Nation is acceptable based on the operation of a system or the use of common controls. The senior agency official for privacy is required to review authorization materials for systems that process personally identifiable information. Before a system is put into operation (or continues to operate), a valid authorization to operate is required."
Learn More About Step 5 From NIST Guidance
RMF Step 6: Monitor
The last step of the Risk Management Framework accounts for today's constantly evolving landscape. Every day new threats, vulnerabilities and technologies appear and organizational mission and business process need to evolve. By requiring continues monitoring programs, the RMF guides an organization through the process of maintaining system authorization within a dynamic operating environment.
Learn More About Step 6 From NIST Guidance
Want To Know More About RMF As It Relates To Your Sales Process?
Register now for our OnDemand Federal Sales Certification Course - Territory Module. This module discusses everything you need to know about RMF and other Federal product certifications you need to sell your solution to the Federal Government.


